موقع اعادة باسورد سيرفر الميكروتيك القديم مغلق
وكلنا كنا بنشتكى من اننا مش عارفين نرجع الباسورد لو فيه بيكب
كتير مننا ساعات بينسى باسورد الميكروتيك
بس بيكون محتفظ ببيكب
لازم تحفظ الموضع اللى اشترح النهاردة ده
علشان بكرة هاتتزنق له جاااااااااااامد اوى
بس بلاش نستغله فى تهكير الشبكات؟..xd
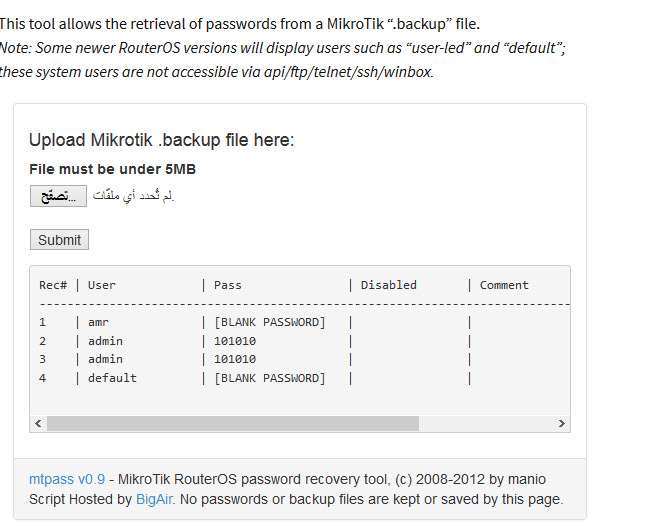
This tool allows the retrieval
of passwords from a MikroTik
“.backup” file.
Note: Some newer RouterOS versions
will display users such as
“user-led” and “default”;
these system users are not accessible
via api/ftp/telnet/ssh/winbox.
شاهد شرح كيفية عمل الموقع
رابط الموقع المستخدم فى الشرح
معاينة
تحياتى لكم
شادى سوفت
فكرة عمل الموقع تعتمد على الدرس ده
MikroTik Password Recovery
last update: 2012-11-28
WARNING: The author makes no guarantees and holds no responsibility for any damage, injury or loss of property that may result after reading this page. Following text is for education purposes only!
Information on this page as well as mtpass tool are intended to help (to recover password(s) without loosing configuration) mikrotik administrator and/or owners *ONLY*. Using it for other purposes (ie. to networks) is breaking the law!
According to information on MikroTik's wiki page, it is not possible to recovery the passwords without loosing configuration. It is not true - i'll try to proof that below :)
News
2012-11-28: new mtpass release: mtpass-0.9.tar.bz2 (fixes compilation with gcc 4.7.2)
2012-08-11: added info about kernel image for RB411-5nH
2012-01-29: new mtpass release: mtpass-0.8.tar.bz2 (another fixes for decoding new RouterOS files)
2011-08-15: new mtpass release: mtpass-0.7.tar.bz2 (kocour_easy: fix for decoding files from RouterOS 5.5)
2010-10-12: new mtpass release: mtpass-0.6.tar.bz2 (fixed compilation problems with newer g++)
2009-12-17: added info and image for RB411 with AR8012 ethernet chip
2009-10-06: added info about RB1xx
2009-03-26: new mtpass release: mtpass-0.5.tar.bz2 (fixed decrypting passwords longer then 16 chars)
2009-03-17: new mtpass release: mtpass-0.4.tar.bz2 (lot of fixes, able to decrypt passwords from mikrotik backup files and full flash-dump files)
2008-12-13: added info about RB411
2008-12-08: new mtpass release: mtpass-0.3.tar.bz2 (figured out and implemented crypto algorithm - no more collecting xor keys)
2008-01-23: new mtpass release: mtpass-0.2.tar.bz2 (now it can decrypt passwords for all users)
Hardware needed
- computer (laptop is a good choice for hard conditions) :)
- RouterBoard (i've tested it on versions: 532, 532A and 411 - but should work on all OpenWrt-supported RouterBoards, Cesco tested it on RB133C)
- serial console cable
- patch-cord
Soft needed
- Due the fact that i don't like the big bill's operating system, so this tutorial will be based on linux, the distribution should not matter, but it's based on debian
- dhcp server (isc dhcp was used)
- tftp server (tftp-hpa was used)
- minicom (for serial communication)
- netcat
- ... and my mtpass tool :)
So here we go...
Our goal is to set the RouterBoard BIOS to boot the system via network. In this way we will load our custom kernel. With that kernel we will be able to send to computer a file with MikroTik passwords. Then we will be able to decrypt the passwords.
1. Minicom configuration
If we don't chage default settings - the RouterBoard's console port should be accessible with the following transmission parameters: 115200, 8N1. So we need to set MikroTik like that. If minicom is launched for the first time, there's need to setup: # minicom -s Select "Serial port setup" and a window with parameters should appear. In my case i set:
A - Serial Device : /dev/ttyUSB0
E - Bps/Par/Bits : 115200 8N1
F - Hardware Flow Control : Yes
G - Software Flow Control : No
I've set the /dev/ttyUSB0 as serial port, due using a USB<->RS232 converter. In the case of computer with a standard COM1/COM2 port, so you should of course set the path to /dev/ttyS0 or /dev/ttyS1
After setting, you need to accept these values with hit the Enter key, then you'll return to main menu. Now you need to save minicom configuration as default:
"Save setup as dfl" and we're ready with minicom.
2. dhcp and tftp server configuration
You should setup dhcp to assign the IP address to MikroTik and then to pass the server and path to kernel image, which will be booted. How to configure the dhcp server is a topic for different kind of article, so I'll confine to minimum needed information :)
i used the following dhcpd.conf file:
default-lease-time 21600;
max-lease-time 43200;
option domain-name-servers 10.0.0.1;
option netbios-name-servers 10.0.0.1;
option netbios-node-type 8;
option www-server 10.0.0.1;
authoritative;
allow booting;
allow bootp;
subnet 10.0.0.0 netmask 255.255.255.0
{
option routers 10.0.0.1;
option subnet-mask 255.255.255.0;
option broadcast-address 10.0.0.255;
filename "/tftpboot/linuxrc";
range 10.0.0.10 10.0.0.100;
}
You need to copy the linuxrc file to /tftpboot/ directory. This file is a kamikaze OpenWrt firmware. I've compiled it with ramdisk support - it doesn't need to put on CompactFlash, because this is the not point (I don't want to make changes to MikroTik filesystem itself - so i need to boot the OpenWrt from ramdisk). The image has also hardcoded IP address for eth0 interface (10.0.0.10).
If you want to compile the kernel and OpenWrt by yourself here is a link for a configuration file: .config (prepared and build with kamikaze version 7.09)
Kernel for RB411: If you have RB411 you need other kernel file (which you need to put as /tftpboot/linuxrc):
http://wifi.ozo.com/airo/openwrt/firmware/kamikaze/2.6/ar71xx/12846/openwrt-ar71xx-vmlinux-initramfs.elf
Kernel for RB411-5nH: As reported by Igor K., if you have RB411-5nH you need the following kernel file (which you need to put as /tftpboot/linuxrc):
http://www.ozo.com/airo/openwrt/firmware/latest/2.6/ar71xx/26878/openwrt-ar71xx-nand-vmlinux-initramfs.elf
Kernel for RB411 with AR8012 ethernet chip: Thanks to Mirek i found out, that there are RB411 with different ethernet chip (AR8012 instead of KSZ8041NL)
more info about it: https://forum.openwrt.org/viewtopic.php?id=22776
He compiled and tested password recovery on such hardware using his OpenWRT firmware: openwrt-ar71xx-vmlinux-initramfs.elf
Kernel for RB1xx: Cesco compiled kamikaze 8.09 for Infineon ADM5120 (it should work on any RB1xx RouterBOARD) - so if you have such a hardware - download it and put it as /tftpboot/linuxrc:
openwrt-adm5120-vmlinux.elf
NOTE: Sometimes (if tftp server is chrooting into /tftpboot/ after start - like in Fedora tftp-server) you need to have a path relative to mentioned directory - so in that case you need to have line:
filename "/linuxrc";
3. Let's do it :)
The following text is based on RouterBoard 532 (i've also tested it on 532A and 411).
We connect the mikrotik with computer via serial console cable and via patch-cord, but we have to connect it to main ethernet adapter - in my RB there's a "PoE" sticker. If you have not do that already it's time to configure ethernet interface and launch the dhcp server on computer:
# ifconfig eth0 10.0.0.1 up
# invoke-rc.d dhcp start
Now it's time to run a minicom without modem initialization (this is not needed at all):
# minicom -o
If MikroTik is now running you need to reboot it, and if doesn't you need to power it up - short after that you should see on console the RouterBoard's BIOS:
RouterBOOT booter 1.5
RouterBoard 532
CPU frequency: 264 MHz
Memory size: 32 MB
Press any key within 1 seconds to enter setup
You have a short time to hit any key (default: one second - can be changed later) and than you'll see:
RouterBOOT-1.5
What do you want to configure?
d - boot delay
k - boot key
s - serial console
o - boot device
u - cpu mode
f - try cpu frequency
c - keep cpu frequency
r - reset configuration
g - upgrade firmware
i - board info
p - boot protocol
t - do memory testing
x - exit setup
your choice:
press o:
your choice: o - boot device
Select boot device:
e - boot over Ethernet
* n - boot from NAND
c - boot from CF
1 - boot Ethernet once, then NAND
2 - boot Ethernet once, then CF
b - boot chosen device
your choice:
If you have a system on NAND memory you need to choose:
boot Ethernet once, then NAND - (1)
else - if you boot from CF (asterisk next to 'c' selection) then you need to press 2.
In my case i've pressed 1 and i was back in main menu.
Then i've selected the boot protocol configuration (p):
RouterBOOT-1.5
What do you want to configure?
d - boot delay
k - boot key
s - serial console
o - boot device
u - cpu mode
f - try cpu frequency
c - keep cpu frequency
r - reset configuration
g - upgrade firmware
i - board info
p - boot protocol
t - do memory testing
x - exit setup
your choice: p - boot protocol
and i've selected dhcp (2):
Choose which boot protocol to use:
1 - bootp protocol
* 2 - dhcp protocol
your choice: 2 - dhcp protocol
After return to main menu you need to press x to save settings and reboot the kernel from your computer:
RouterBOOT-1.5
What do you want to configure?
d - boot delay
k - boot key
s - serial console
o - boot device
u - cpu mode
f - try cpu frequency
c - keep cpu frequency
r - reset configuration
g - upgrade firmware
i - board info
p - boot protocol
t - do memory testing
x - exit setup
your choice: x - exit setup
writing settings to flash... OK
RouterBOOT booter 1.5
RouterBoard 532
CPU frequency: 264 MHz
Memory size: 32 MB
Press any key within 1 seconds to enter setup.
writing settings to flash... OK
trying dhcp protocol... OK
resolved mac address 00:1B:FC:41:BE:43
Gateway: 10.0.0.1
*transfer started ................................ transfer ok, time=1.8s
setting up elf image... OK
jumping to kernel code
[ ... a lot of debug kernel output here ... ]
init started: BusyBox v1.4.2 (2008-01-15 11:43:12 CET) multi-call binary
Please press Enter to activate this console. PPP generic driver version 2.4.2
After enter we have a OpenWrt running on MikroTik:
BusyBox v1.4.2 (2008-01-15 11:43:12 CET) Built-in shell (ash)
Enter 'help' for a list of built-in commands.
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
KAMIKAZE (7.09) -----------------------------------
* 10 oz Vodka Shake well with ice and strain
* 10 oz Triple sec mixture into 10 shot glasses.
* 10 oz lime juice Salute!
---------------------------------------------------
root@OpenWrt:/#
If you have problem like "flash write..error 0x0" or something similar, then set dhcp protocol like above and after that in boot device menu select:
"e - boot over Ethernet", and then press "b - boot chosen device"
4. Mounting
Now it's time to mount NAND memory and send a file with passwords. You may check for sure if kernel correctly found a NAND chip. If you can't see it on screen, then type:
# cat /proc/mtd
dev: size erasesize name
mtd0: 00400000 00020000 "RouterBoard NAND Boot"
mtd1: 07c00000 00020000 "RouterBoard NAND Main"
The above result is for my 128MB memory chip - i don't know how should it be for other capacities :(. At this stage you need to know a important thing: i don't know if it's true or not but i heard that when you mount the NAND (even in read-only mode) it is a risk that the data on chip can be damaged. Fortunatelly it wasn't happend in my case - but it doesn't meen you'll be lucky too and keep in mind, that you've been warned!
So - it's time to mount the NAND memory chip (in read-only mode): # mount -t yaffs2 -o ro /dev/mtdblock1 /mnt NOTE: in RB411 i've got this partition scheme: Creating 3 MTD partitions on "NAND 64MiB 3,3V 8-bit":
0x00000000-0x00040000 : "booter"
0x00040000-0x00400000 : "kernel"
0x00400000-0x04000000 : "rootfs"
... so I need to mount /dev/mtdblock2 instead of /dev/mtdblock1
File system should be mounted right now. The crypted passwords for MikroTik users are in /mnt/nova/store/user.dat (in newer RouterOS versions in: /mnt/rw/store/user.dat) file.
It's need to send that file to computer, and then decrypt the password. I used a simple method to do that: netcat tool. All you need to do is send that file from MikroTik and receive on computer.
You need to run netcat on computer in listening mode - ie. on port 7878: /bin/netcat -l -p 7878 > user.dat ... and from MikroTik you can send a file: cat /mnt/nova/store/user.dat|nc 10.0.0.1 7878 In this simple way we have on computer the intrested file. The next boot of mikrotik should be the standard way - from that medium we set before.
Now you can disconnect cables from MikroTik :)
The alternative way (tip by Adriano Provvisiero): you can just hexdump content of user.dat file from openwrt and copy/paste the output from screen to a text file on the box where you are going to run mtpass. After that, just run: xxd -r TXTFILE > user.dat and run mtpass on the output user.dat as normal. Xxd will revert the hexdump to binary and avoid you the hassle of needing a working ethernet driver or finding your way around a serial transfer of the user.dat.
5. 283i4jfkai3389 - what the hell is going on... :)
The passwords in the sended file are crypted - fortunatelly it's not too hard to decrypt it - after my analysis I figured out that the passwords are crypted with XOR method. Every account has a different crypt-key.
I wrote a small tool, which take filename with passwords as first argument (user.dat in our case), then it writes a passwords to standard output. The tool was tested on three different MikroTiks and it seems that is working correctly - but i don't guarantee that the RouterOS crypting algorithm will not change in the future and even with different versions. If it doesn't work in your case please mail me - i'll try to check why in my spare time.
Unfortunatelly for now i still don't know the crypt-key algorithm so my tool include known keys only - if you're in luck you'll see decrypted passwords - or strange characters otherwise.
Update (2008-12-08): after a long time when xor key generation algorithm was unknown to me i finaly have some time and i figured out that algorithm: to username is concatenated a constant string: "283i4jfkai3389", then from this is computed md5 digest, which is in fact the xor key, which we need for decrypting :)
simple, isn't it? :) I implemented it from mtpass-0.3 version.
Sources of this tool are available here: mtpass-latest.tar.bz2, therefore you need to unpack, compile and run it.
The openssl development libraries are required. On ubuntu and debian the package is called libssl-dev.
Finally - you can launch it:
# ./mtpass user.dat
mtpass v0.3 - MikroTik RouterOS password recovery tool, (c) 2008 by manio
Reading file user.dat, 166 bytes long
Rec# | Username | Password | Disable flag | User comment
--------------------------------------------------------------------------------------------
1 | admin | secretpass | | system default user
And you have what you're looking for :)
I hope this tutorial was helpful and you have your NAND ok after that :)
Best regards. And for happy ending a several links...
Credits:
I want to thanks the following people for support, time and testing:
Drasar, Andrew Griffiths, Mustafa Kemal, Claudio F., Sinisa Durutovic, Cesco, Mirek, kocour_easy, NetworkPro, mthqwork
Password recovery from backups:
It may happend that you loose/forgot the password but fortunately you made a backup file some time ago. Backup files are made by RouterOS and saved in format:
MikroTik-DDMMYYYY-HHMM.backup
From 0.4 version mtpass is able to recover password from backup files too. You only need to pass a backup file name argument, like this:
# ./mtpass MikroTik-02082008-1346.backup
Similar situation is when you have a full flash-dump file, for instance /dev/mtdblock (look above at point 4). The mtpass should also be able to recover lost passwords.
Links:
- MikroTik Router Security Analysis: Insecure Network Protocol
- MikroTik Router Security Analysis: Uncovering a hidden kernel module in a binary
- MikroTik Router Security Analysis: Weak password storage / encryption
- OpenWrt
- RouterBOARD 500
- RB500 Linux SDK
- Installation of Debian Sarge on Rouberboard 532



0 تعليق على موضوع : password recovery tool حل مشكلة ضياع باسورد سيرفر ميكروتيك موقع باسورد ميكروتيك بيكب mikrotik.backup
الأبتساماتأخفاء الأبتسامات